Today’s security challenges at the tactical edge
Traditional tactical communication networks use proprietary radio and crypto-technology to secure information transmission. Frequently used are pre-shared keys and hard-coded crypto-chips embedded in radio equipment.
The result: vendor specific silo solutions, incompatibility and lack of economy of scale. This represents a challenge for the introduction of innovative, emerging broadband technology such as 5G at the tactical edge.
GuardStack
augmented Security
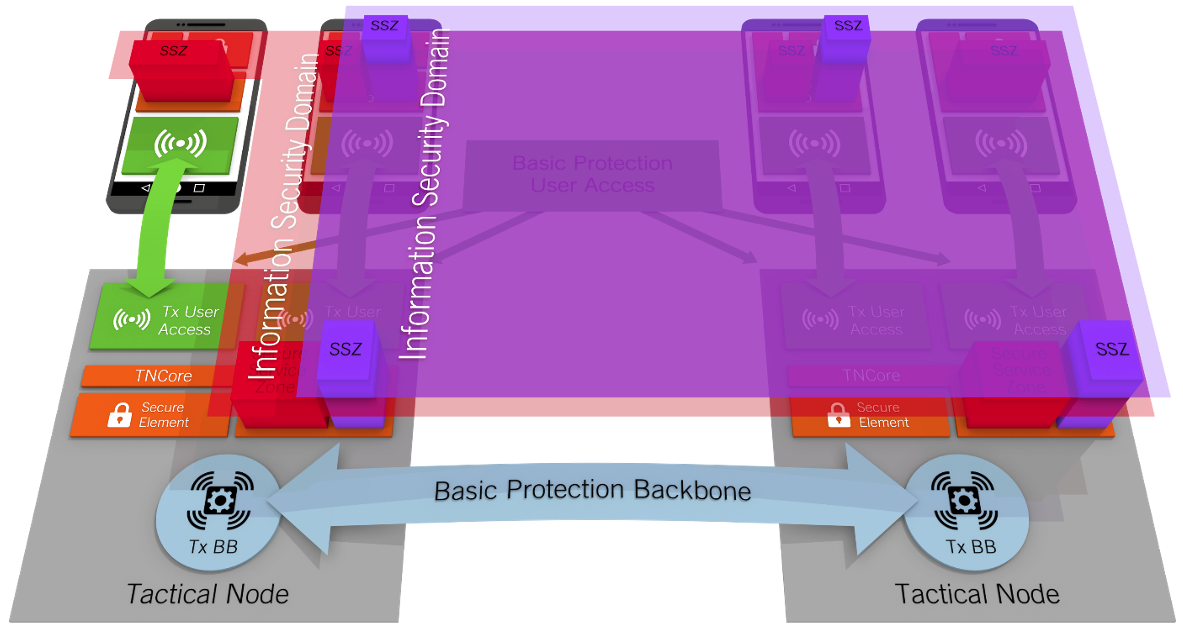
GuardStack Security creates an end-to-end overlay of secure information domains, providing secure container environments for applications at the far edge client and the server side. This end-to end security overlay concept eliminates the requirement for proprietary radio and crypto-technology and paves the way for an open communication infrastructure and corresponding innovation without compromising data security. Classified information domains are accessed based on strong authentication methods with secure hardware elements.
Encryption Overlay for unclassified transport
GuardStack enables the usage of unclassified transport networks with classified end-to-end information encryption.
Multiple Security Domains
GuardStack features multi-level security domains across the end-to-end network from the tactical core servers to the actual client smartphone devices.
Secure Hardware Elements
A combination of modern encryption methods and secure hardware elements guarantee end-to-end security even in zero-trust environments.
Decentralized Group Key
Our unique group key method eliminates the need for a centralized key coordinator, contributing to effective MANET operations.
Custom Android
A customized Android smartphone, meeting the highest security requirements, provides full control of all communication services.
Trusted Source Code
Our source code is 100% government trusted, providing federal customers full transparency and control.
Data Sheet